March 22, 2021
I was concerned about the heart patient they cooled to absolute zero. He looks 0K now.
Guest Author – today’s Monday Byte is provided by Gaylynn Fassler, an Information Security Analyst in the Duke Health Information Security Office. Gaylynn manages the monthly Phishing Exercise.
![]() Have you ever received an email and thought, “that seems suspicious” or “that doesn’t seem correct” or “why am I getting this?” Did you click on the link or respond to the email anyway?
Have you ever received an email and thought, “that seems suspicious” or “that doesn’t seem correct” or “why am I getting this?” Did you click on the link or respond to the email anyway?
Phishing attacks are the most prevalent threat user’s face today. Here at Duke, we have a myriad of tools that prevent millions of emails a month from getting to you, but our users are still our most important line of defense. Phishing most often comes by email, but it can also come through text messages, phone calls, and social media.
Duke Health started the simulated phishing program in late 2019, and we are very grateful to DUSON who joined the program in January of 2020. DUSON was our first opt-in entity, and your partnership has been invaluable to growing our program.
We have several main goals with the phishing program:
- Increase awareness of the dangers of phishing
- Educate users how to recognize suspicious emails
- Enable our users to report suspected phishing emails
These goals support our ultimate mission of keeping Duke Health and all our data safe and secure.
Every time you get an email, there are a few questions you can ask yourself right away:
- Do I know the sender?
- Was I expecting it?
- Do I feel rushed or pressured?
- Is the request unusual?
For example, if you get an email from your boss that is asking you to go buy $1000 in Amazon gift cards, scratch off the backs, take pictures and send the pictures to them in an hour, your decision tree might look like this:
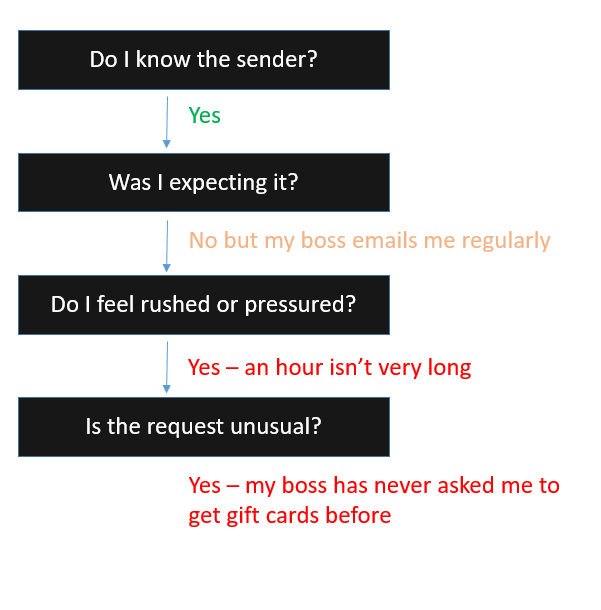
Once you go through the decision tree, you realize you feel rushed/pressured and the request is unusual, which should be an indicator to look more closely at the email.
The first thing to check would be the senders email address. It might look like its coming from your boss, but if you hover over the name, you might see something like yourboss.duke@gmail.com as the senders address. That should be a huge red flag, and is likely an indication of an impostor.
Another good action to take is to contact your boss outside of the email. Call them at a phone number you know, or email them at their Duke email address and ask if they sent the request. Members of the Duke community have fallen for these kinds of schemes, and we don’t want that to happen to you.
For another example, what would your decision tree look like if you got an email from a coworker with a link to a YouTube video they thought you might enjoy? It might look like this:

This is where it gets tricky. You know the sender and they’ve sent you this kind of link before. It is most likely legitimate and safe, but it never hurts to be certain. In this case, you should hover your mouse over the link, which will allow you to see where the link really goes.
For this, you would expect the link to look something like Youtube.com/video. If the link looks like qquio.com/watch or brendaluvsdylan.metflix.com, it should raise your suspicions. This would a good time to double check the sender, and possibly reach out to that coworker.
* An important note about hovering over the links: it’s really hard to do on a mobile device. If you get an email that feels off, wait until you’re back at your computer before hovering over the link. Also, here at Duke we have a URL re-write tool, so the hover link always starts with “https://urldefense.com/V3/_”. If you are trying to tell where the link goes, that information starts after the underscore.
We’re not trying to trick you or make you feel bad when we send our simulated campaigns. Increased awareness of how to spot, analyze and report suspicious emails is one of the ways that we all help keep Duke Health secure.
Industry research, as well as our own metrics, shows that consistent training reinforcement via simulated phishing exercises greatly improves user’s awareness and response to suspicious emails. We’re not trying to train you to spot our emails, but are trying to arm you with the knowledge and tools to spot any suspicious email and know how to react.
The most valuable thing we can teach you is to trust your gut: if something seems suspicious or too good to be true, it probably is. It is ok to be wary or suspicious and ask for verification or more information. And we hope you take these lessons into your personal life: phishing emails are not specific to Duke or your work email, but are often sent to your personal accounts as well.
If you have any questions about phishing, or security in general, feel free to reach out to security@duke.edu.
Missing Our Campus?
Our Duke Photo of the Week is the Duke Blue Devil Tower. What better location to get your COVID vaccine than overlooking Brooks Field at Wallace Wade Stadium! It’s easy to find – walk through the Abele Quad to K-Ville and look for the football stadium. Here’s the view while taking your shot …

