In 2024, the project team expanded the monitoring fabric for the MISTRAL project. The hardware infrastructure was expanded from a single sensor node to 20 sensor nodes and dedicated switching hardware for tagging and load balancing scientific network captures.




In support of MISTRAL, OIT is deploying a network monitoring fabric designed to aggregate copies of production traffic from strategically placed optical taps and Switch Port Analyzer (SPAN) port-mirroring sessions. As illustrated in the figure below, the current data sources include parts of our research computing data center network, the Cryo-EM microscope at the Shared Materials Instrumentation Facility (SMiF), and centrally located light sheet fluorescence microscopy devices. Additionally, the campus firewall has been tapped to provide visibility into inter-VRF traffic, and will integrate with VCM, a dynamic environment that offers virtual machines to faculty and students for research and instruction.

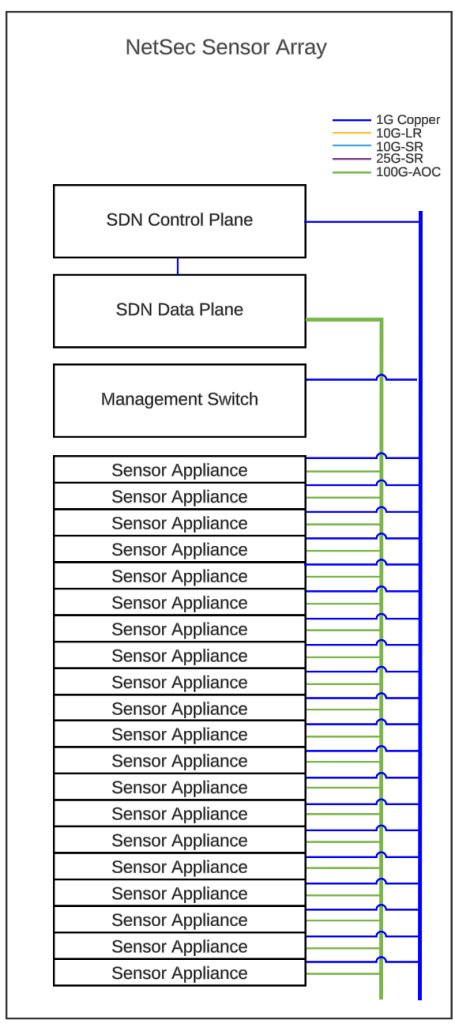
The network security sensor array supporting MISTRAL, illustrated in the figures below, will scale to accommodate 20 Archipelago-style (OAC-1925550) sensor nodes. An SDN data plane receives traffic from passive optical taps and SPAN ports, symmetrically hashing this traffic for efficient delivery to the sensor array, ensuring horizontal scalability. Traffic is not only distributed to physical sensors but also to containers within those sensors, which are mapped to PCIe SR-IOV virtual functions on 100Gb/s NICs. This method reduces software switch overhead within the sensor node, ensuring more CPU and memory resources are available for containerized sensing applications.

The MISTRAL sensor array was also utilized to troubleshoot a data center Network Attached Storage (NAS) issue. In this case, traffic from 100G switches within the data center, supporting both the NAS and some research computing workloads, was SPANned to the monitoring fabric and sent to the MISTRAL netsec sensor nodes for analysis, as shown in the figure below.
